.jpg?width=1160&name=GettyImages-1133767597%20(1).jpg)
Today’s post-production teams are often highly distributed, with team members scattered across towns, cities, and even time zones. Fortunately, collaboration technology has made huge advances over the past few years, making working with your far-flung colleagues as seamless as working with someone in the next room.
Although collaboration technology1 has revolutionized how we work, it has also helped open up the floodgates for potential data breaches. In 2020, when millions of workers suddenly pivoted to remote environments, security experts marked a significant increase in cyberattacks2, including phishing, ransomware, and brute-force password attacks, often enabled by poor cyber hygiene, lax password protocols, and unsecured remote access points.
In fact, a report by the Identity Theft Resource Center3 states that data breaches increased by 68 percent in 2021. These 1,862 security events surpassed the number of breaches in 2020 (1,108) as well as 2017’s record of 1,506.
Effective data protection is crucial for video production projects.
The media and entertainment industries have always been popular targets for hackers and other malicious users. But with cyberattacks on the rise and remote work environments likely here to stay, it has never been more important to make sure your collaboration software is secure enough to meet the challenge.
It has never been more important to make sure your collaboration software is secure enough to meet the challenge.
Some of the more common threats video post-production teams encounter include:
- Intellectual property theft
- Unauthorized access to files
- Accidental or malicious file corruption
- Ransomware
Depending on the type and the extent of the media breach, the consequences can be devastating to you and your clients.
For example:
- File encryption/deletion can delay post-production work and require expensive remediation to restore lost or damaged footage.
- Exposure of personal data can result in compliance penalties, fines, and legal fees.
- Leaked film footage can reduce potential revenue and impact the success of the asset.
- All of these scenarios can cause irreversible reputational damage to your brand, resulting in loss of customers—both current and future.

Look for these security features in collaboration software.
With security being a key requirement for your collaboration software, it’s important to find a solution that is tailored to the specific security and productivity needs of post-production teams.
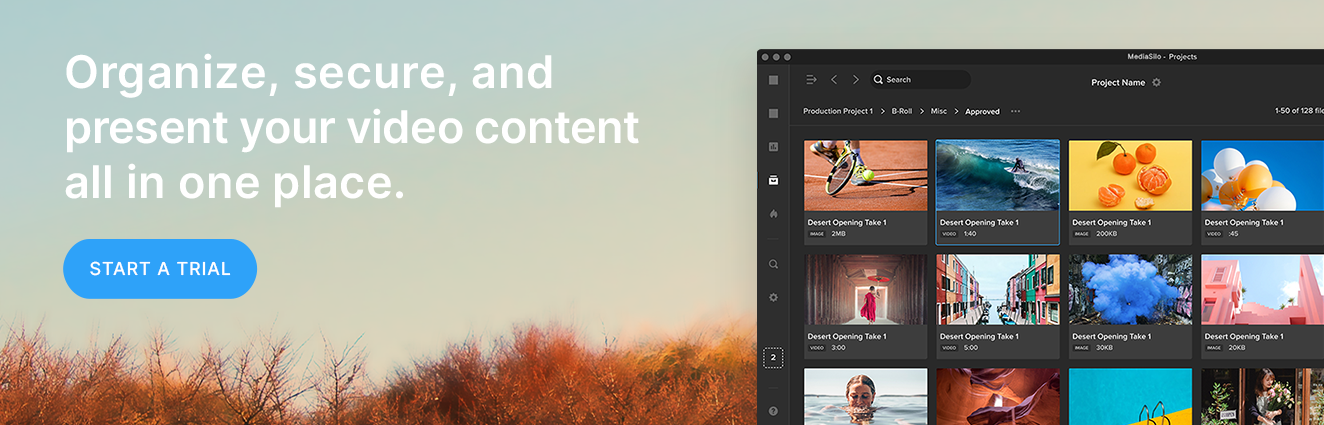
MediaSilo studio-grade technology makes asset security a priority with three key capabilities:
1. Watermarking
Video watermarking is an effective way to deter unauthorized release of assets, track who is viewing and sharing content, and indelibly brand your shared content. MediaSilo’s SafeStream watermarking technology provides enterprise-grade security for your assets at multiple levels:
- Visual watermarks: User-specific information is burned directly onto the video to create a robust layer of theft deterrence.
- Forensic watermarks: Invisible tags trace a video to the user who requested playback, making it possible to trace leaks to the source.
- Ad-hoc watermarking: Send review links with custom watermarks for one-off use cases.
- Workspace or project-level watermarking: Create watermarking standards for specific projects or entire workspaces.
2. Role-Based Security
The post-production process requires the input of many different people—from video editors and sound technicians to graphic designers and visual effects artists. And while all of the players will need access to the project files, not every user needs the same level of access.
While all of the players will need access to the project files, not every user needs the same level of access.
Role-based provisioning lets the project administrator define who can access what and when by assigning permissions for standard or customized roles to provide flexibility and control over what a user can do in a given project.
For example, the project owner can delete a project, modify watermark settings, invite users to a project, or modify a user's role within a project while an internal collaborator can only view, edit, and share assets within the team.
In addition to limiting permissions by roles, lifecycle policies can be used to set expiration dates for project assets and review links to control who has access to what and when.
3. Access Management
With so many employees now working outside of the traditional firewall, organizations are having to change tack and make the people the perimeter.
There are several ways to add additional layers of security to ensure only authorized users have access to your collaboration platform:
Multifactor authentication (MFA)
MFA requires credentials to be verified by more than a password alone. For example, when logging in, a user may be asked to enter something they know (a password) as well as an additional code sent to their phone or email.
Single sign-on (SSO)
SSO lets a user log in to multiple applications with one set of credentials. This increases security because it reduces the number of potential entry points (i.e., attack surfaces) for malicious users.
Passwordless login
This security approach creates a one-time link that confirms browser and machine identity each time before granting access tokens for login, and removes the possibility of a password being hacked or stolen.
Turn to MediaSilo to protect your assets.
Preventing data and media breaches is a top priority for every post-production team. MediaSilo’s secure collaboration technology can help ensure assets are only accessible by the right users and that videos are watermarked for protection against unauthorized sharing and leaks.
1: https://cisomag.eccouncil.org/security-gaps-in-collaboration-apps/